How to have good password hygiene
Learn how to have good password hygiene to avoid having your identity stolen or your accounts compromised using password managers, 2FA and email aliases.

In this article, I'll be going over my personal 'good password hygiene' steps and explain how they can avoid being hacked. Account compromise can result in financial losses and identity theft. Here's how you can minimise these risks.
Basics of User Accounts
A user account is generally a record of a user on a service. Usually, after registering, you are required to provide a username (or often an email address) and a password. If the ones entered match at a services' database, you are granted access.
How your details could be compromised
There's various ways this can happen, but the most common are either a phishing attack or a database compromise where your details are shared outside of the organisation that you were registered with.
What is a Phishing attack?
The phrase 'phishing' means another website is masquerading to be a service which you are familiar. These will look exactly like the familiar login for a given service, except when you enter your details, these are submitted to a malicious party, rather than the service you are wishing to log in with.
A usual tell-tale give-away is by checking the URL, if it's not the service you expect, then don't enter your details.
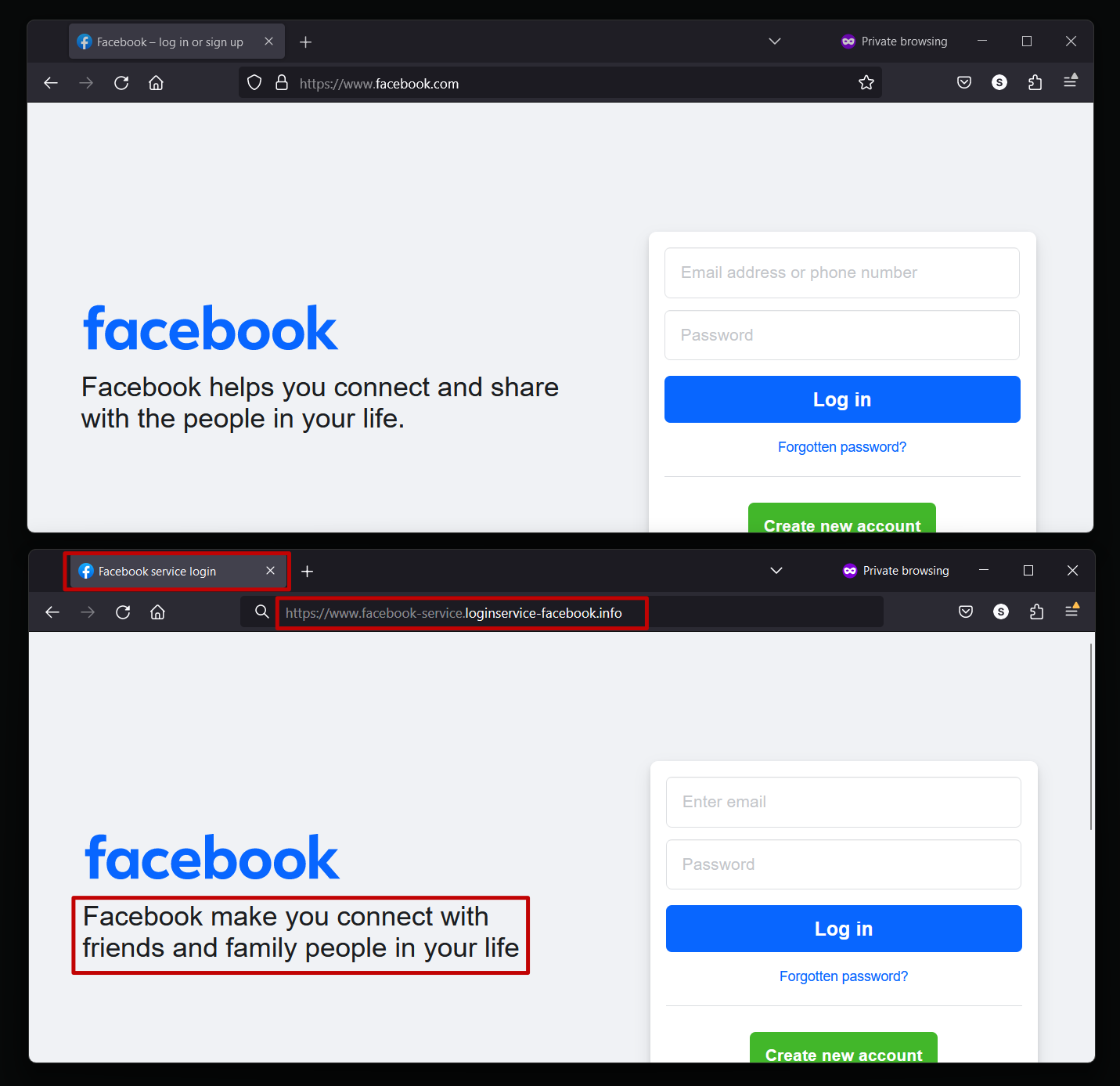
In the example above, we can see the Facebook login page, which is served by the domain 'www.facebook.com' versus a phishing page masquerading as Facebook by a bad actor. Although they look near identical, there are some indicators that not all's right:
- The title shown in the tab reads 'Facebook service'. Generally, you'd not see the use of 'service' on a genuine page.
- The URL shown in the URL bar reads 'www.facebook-service.loginservice-facebook.info'. This is not Facebook's URL and you should only use any form served from the domain you're expecting (in this example, facebook.com).
- Phishing websites often contain poor English or bad grammar. This is usually due to phishing attacks originating from territories where English isn't the first language. This isn't always the case, but certainly something to look out for.
How do I check if a service is genuine, or an email address that I receive is genuine?
I built a service for that! Look for the tell-tale signs as discussed previous, but if you wanted to check a domain, an email address or a URL to see if it's previously been identified as being used for phishing attacks, use Dracoeye, which goes away, checks with various security tools for indicators of compromise. Read about what my Director of Technology had to say about conceiving the idea.
What is a database dump or database leak?
Systems generally store login information in a database. Good development practices mean that the password is encrypted before it is stored. This means, if the database is compromised, the data is meaningless to the hacker without the encryption keys to decrypt the data.
Not all services are created equally, and too many times in the past, sensitive user information, including usernames, email addresses and passwords are stored in 'plain text', meaning there's no effort of obfuscate these details.
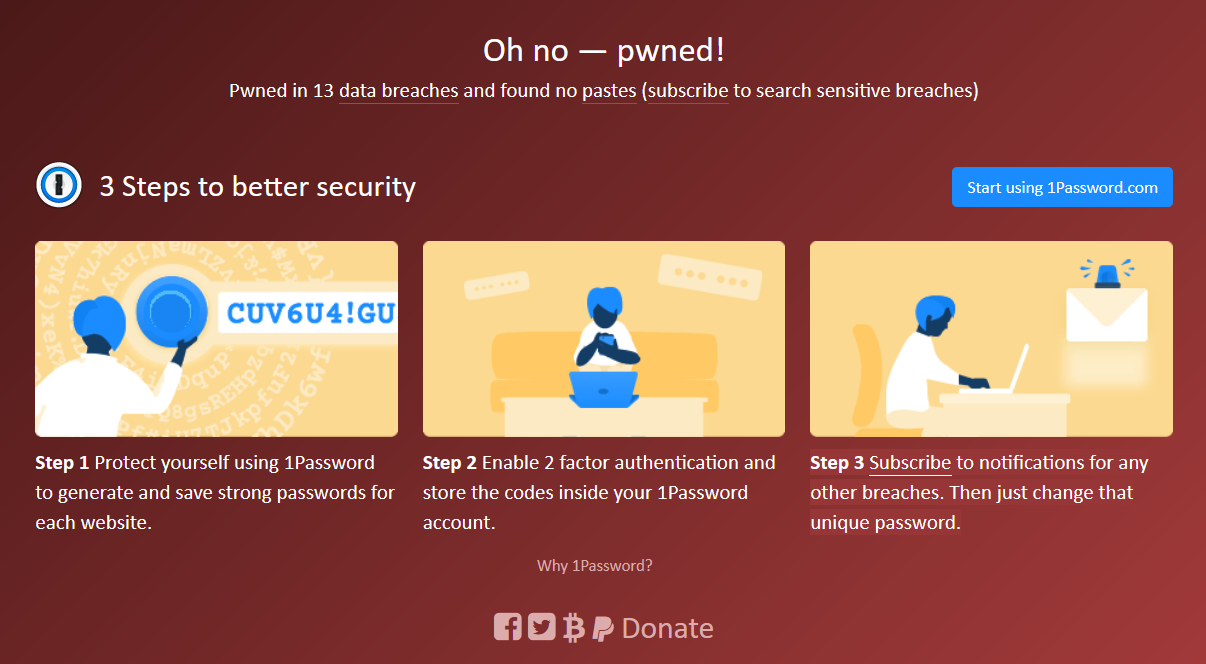
How do I know if my details were leaked by a hack on a service I use?
My go-to resource for this is 'Have I Been Pwned?'. They will search data dumps for your email address and indicate whether or not you were included in a service compromise.
Why you shouldn't use the same password between services
Most people use the same password, or variants of the same password across many services, including their email accounts. With the trend for services to require an email address and a password to login, these same credentials will work across multiple services when the same password is used, increasing the risk of compromise across multiple services. Let's explore this as a scenario.
Janet uses the same email address and password for most things
Janet is a woman who is mad about her faithful dog, Fluffy, who joined the family in 2014. Her email address is [email protected] and her password is Fluffy2014# which she uses across most services to make life easier when logging in.

Janet is keen to learn about her family in Scotland, so is a member of the well-known website Ancestry.com. A year later in 2015, Ancestry suffered a catastrophic hack which exposed the details of 297,806 accounts in plain text, including email addresses passwords, names etc. Janet's details were exposed in this.
Janet learns of the hack in an email from Ancestry themselves, and promptly changes her password to Fluffy2014#1. Problem solved, right? Wrong.
A day later, Janet cannot log into her Gmail account. She learns from friends and family members that emails have been sent from her account saying she's been stranded and urgently needs money to get a hotel room, along with a link to a PayPal account that doesn't belong to her. Her friends, understanding she is stuck, promptly begin sending money, which actually goes to a hacker.
How did they get into her account? From the leaked data from the Ancestry hack, the hackers learn that she uses Gmail as her service provider. Janet used the same password for her gmail account and her Ancestry account, allowing he hackers to login and change her password. But it gets worse.
The hackers trawl her emails and discover emails from her bank. They can see emails she sent to her mother, Susan. They know from her email address, she was likely born in 1978 and found her home address, all the details they need in order to pass security with her bank and begin emptying her savings. In conjunction to this, they have access to her PayPal account and have begun making purchases.
Poor Janet. Just when things couldn't get worse, they just did. Next she finds that her Facebook and Twitter accounts have also been compromised, but how? She is sure she used a different password for these. The answer is simple. The hackers now control her email account, and can now perform password resets, which send an email link to confirm the new password.
After a lot of stress, Janet regains control of her her email account and uses a completely different password, but her accounts keep getting compromised, despite her taking very careful steps to completely change all her passwords. But how? How could Janet be this unlucky?
The answer to this is simple, Gmail has a facility where you can forward emails to another account, which the hackers put in place to receive copies of any email she receives. They use this to send password reset emails which are forwarded to them, and the pain continues.
But how could Janet have avoided this?
Use a Password Manager to use random passwords
There are many password managers, some being better than others, but are an essential tool for ensuring all passwords are different for every service you register for. Services such as Bitwarden and Keeper encrypt your data, and can be used on your desktop via a browser extension or an app on your phone. These can be configured to auto-fill login forms on iPhone and Android phones.
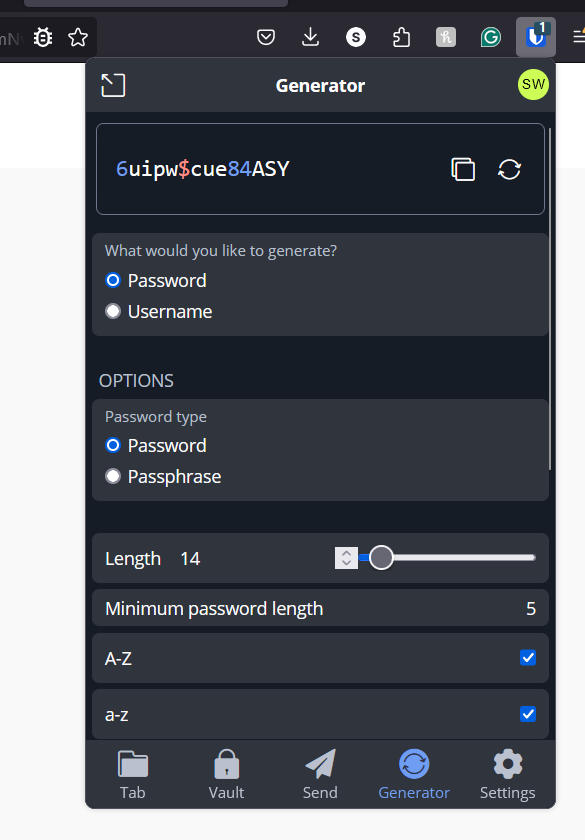
They all essentially work the same. You use one password, completely unique, and the only one you need to remember for your password manager. This allows you to login to these. On mobile devices, you can use your face or fingerprint to login.
Once logged into your password manager, when registering for a service (or changing your password), they have the ability to generate a completely random password. This is then saved so that when you login again, they will auto-fill the login form with these completely random passwords. This reduces the chances of multiple accounts being compromised based on shared passwords.
Unfortunately, not all password managers are equal, with LastPass, a popular password manager being hacked more than once. I can only recommend Keeper or Bitwarden, although others are equally as good, so do your homework.
Password Hygiene
Whether you use to use a password manager or not, basic password hygiene principals should still apply:
- Passwords should be random and not a characteristic of you, your life, your pets or your loved ones
- They should consist of lowercase, uppercase letters, numbers and symbols (ie $%&£@# etc)
- They should be long, 8 characters or more
- Should never be written down, stored in notes applications, especially in conjunction with the service name, username/email and the password itself
Use an email 'plus' alias
It's important to remember, not all email services support email aliases. Furthermore, not all services allow you to register with an alias email, but many do. Luckily for Janet, Gmail does. An alias can be achieved by formatting your email address like this: [email protected]. Mail sent to these aliased email addresses will still be received in your inbox.
When registering for a new service, she can simply suffix her email with whatever she wants, making that email unique to a given service she's registering for. For example, following the Ancestry hack, Janet could choose to use [email protected] instead of [email protected]. Not only does this allow her to learn in future hacks which service was compromised, it means that other services are not easily compromised using her email address.
Using her Password manager, an aliased email and a randomly generated password, hacks can be contained to that one service, saving her a lot of heartache.
Email services that support plus aliases
- Gmail (Google)
- iCloud (Apple)
- Fastmail
- Proton Mail
- Zoho Mail
- Outlook.com (Microsoft)
Two Factor Authentication
Being honest, Two Factor Authentication (commonly called MFA or 2FA) is a complete pain in the arse, but a necessary evil. Many services support 2FA, so should be enabled wherever possible as they limit the ability for a service to be logged into, even if a hacker has your email/username and password.
They work normally by asking for a unique code generated by a authentication app such as Twilio Authy or Google Authenticator when logging in. If the code entered is incorrect, access isn't granted.
Other variants exist, for example, popular gaming platform Steam can be configured to email you your 2FA code, which in the event that your email account being compromised, means hackers can still gain access to your Steam account.
There are a number of other, but similar solutions such as hardware MFA devices such as Yubico, but I won't cover these in this article.
Summary
Account compromises can be incredibly stressful and damaging, not only from a personal level, but from a financial one. Using tools such as password managers in conjunction with 2FA can greatly limit the damage caused by services being hacked, and when coupled with good password hygiene, using strong passwords made up of random numbers, lowercase and uppercase letters and symbols. Throwing in email aliases, you're as protected as what's reasonably possible.

